Unlocking The Power Of AWS Access Keys: A Comprehensive Guide
AWS access keys serve as vital credentials that allow users to interact with Amazon Web Services securely and efficiently. In a world increasingly reliant on cloud computing, understanding how to manage these keys is essential for both individuals and organizations. These keys consist of an access key ID and a secret access key, which together enable programmatic access to AWS services and resources. With the right knowledge, users can leverage AWS access keys to streamline their cloud operations while ensuring robust security measures are in place.
Managing AWS access keys effectively not only enhances productivity but also mitigates potential security risks. When mismanaged, these keys can become a gateway for unauthorized access to sensitive data and services. Therefore, it is crucial to grasp the best practices for handling AWS access keys, including how to create, rotate, and delete them. This article will delve into the intricacies of AWS access keys and provide practical insights for their optimal use.
Whether you are a seasoned AWS user or just getting started, understanding the mechanics of AWS access keys is beneficial. This article will address common questions surrounding AWS access keys, their significance, and the best strategies for managing them. By the end of this guide, you will be equipped with the knowledge needed to navigate the complexities of AWS access keys and enhance your cloud security posture.
What Are AWS Access Keys?
AWS access keys are unique credentials that allow users to authenticate themselves to AWS services. Each key consists of two parts: an access key ID and a secret access key. The access key ID is a public identifier, while the secret access key is a private key that should be kept confidential. Together, they enable users to perform various actions within their AWS account, such as launching instances, managing storage, and utilizing APIs.
How Do AWS Access Keys Work?
The functionality of AWS access keys is rooted in the AWS Identity and Access Management (IAM) system. When a user or application attempts to access AWS resources, they present their access key ID and secret access key for authentication. AWS then verifies these credentials against the account's IAM policies, determining whether the request should be granted or denied. This process ensures that only authorized users can interact with AWS resources, thereby enhancing security.
Why Are AWS Access Keys Important?
AWS access keys are crucial for several reasons:
- Programmatic Access: They enable users to interact with AWS services through the command line, SDKs, and APIs.
- Automation: Access keys allow for automation of tasks and workflows, improving efficiency.
- Security: Proper management of access keys helps safeguard sensitive data and resources.
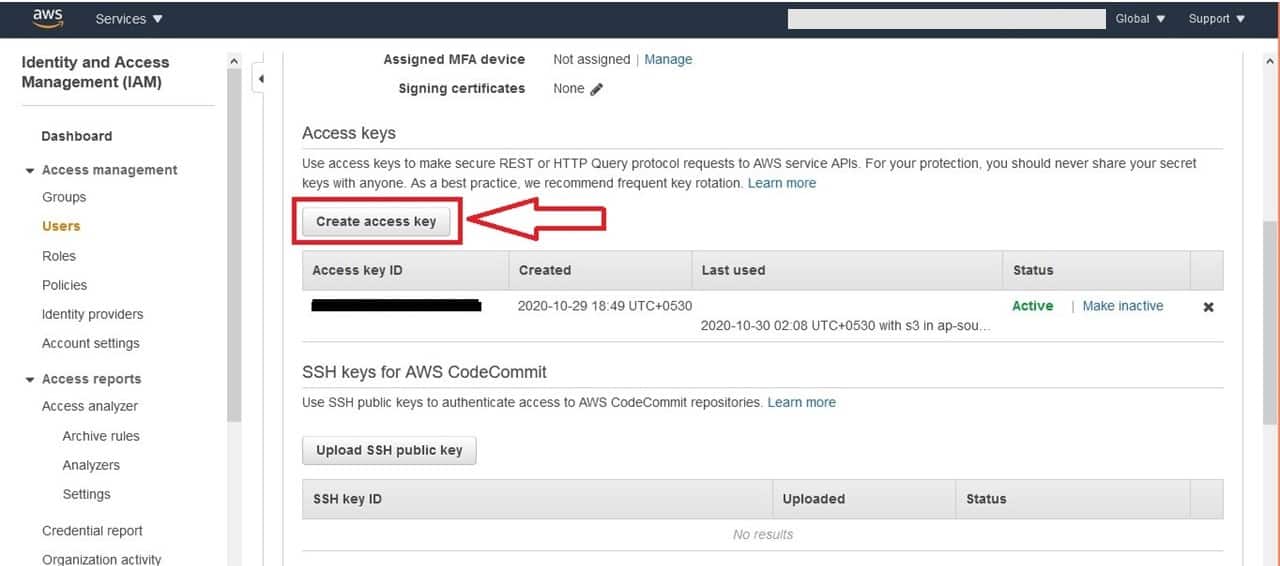
How to Create AWS Access Keys?
Creating AWS access keys is a straightforward process, but it requires appropriate permissions. Here’s how you can create them:
- Log in to the AWS Management Console.
- Navigate to the IAM service.
- Select "Users" from the navigation pane.
- Choose the user for whom you want to create access keys.
- Click on the "Security credentials" tab.
- Under "Access keys," click "Create access key."
- Follow the prompts to create and download the keys.
What Are Best Practices for Managing AWS Access Keys?
To ensure the security and effectiveness of AWS access keys, it is vital to adhere to best practices:
- Rotate Keys Regularly: Regularly changing access keys minimizes the risk of unauthorized access.
- Use IAM Roles: Whenever possible, utilize IAM roles instead of access keys for applications running on AWS services.
- Limit Permissions: Apply the principle of least privilege by giving users only the permissions they need.
- Monitor Usage: Regularly audit access keys to track usage and identify any anomalies.
- Delete Unused Keys: Remove any access keys that are no longer in use to reduce security risks.
How Can You Rotate AWS Access Keys?
Rotating AWS access keys is an essential practice to maintain security. Here is a step-by-step guide on how to rotate access keys:
- Log in to the AWS Management Console and navigate to IAM.
- Select the user whose keys you want to rotate.
- Create a new access key following the steps outlined previously.
- Update any applications or services using the new access key.
- Test the application to ensure it is functioning with the new key.
- Once confirmed, delete the old access key.
What Should You Do If Your AWS Access Keys Are Compromised?
If you suspect that your AWS access keys have been compromised, it is critical to act immediately:
- Disable the Compromised Keys: Go to the IAM section of the AWS Management Console and disable the affected keys.
- Investigate the Incident: Review logs and monitor account activity to understand the extent of the breach.
- Rotate Access Keys: Generate new keys to replace the compromised ones.
- Enhance Security Measures: Consider implementing MFA (multi-factor authentication) and stricter IAM policies.
Can You Use AWS Access Keys with Other AWS Services?
Yes, AWS access keys can be used with a variety of AWS services. They are integral for programmatic access to services such as Amazon S3, EC2, DynamoDB, and many others. Whether you're managing storage, computing resources, or databases, AWS access keys provide the necessary authentication to perform actions securely.
Conclusion: Mastering AWS Access Keys for Enhanced Security
Understanding and effectively managing AWS access keys is essential for anyone utilizing Amazon Web Services. By following best practices, creating and rotating keys securely, and knowing how to respond to potential compromises, users can significantly enhance their cloud security. As cloud computing continues to evolve, staying informed about AWS access keys will empower users to leverage their full potential while safeguarding their valuable resources.
Understanding Ordinal Variables: Examples And Insights
Understanding The Disturbing Actions Of Ed Kemper Towards His Mother
Unlocking The Power Of Indirect Channels Marketing
Create AWS Access key ID and secret access key NerdyElectronics

AWS access keys

Best Practices for Securely Using AWS Access Keys